Public-Key Cryptography and RSA – young log is one of the most viral photos on the internet as we speak. As well as to those photographs, Schematic Diagram Of Public Key Cryptography – Circuit Diagram, Public Key Encryption and Mechanism of Public Key Cryptography | Download Scientific Diagram additionally experienced a significant increase in search developments. If you’re searching for viral pictures associated to Public-Key Cryptography and RSA – young log, on this page now we have 35 images for you to discover. Here you go:
Public-Key Cryptography And RSA – Young Log

younghk.github.io
cryptography rsa cryptosystem
Public Key Cryptography Algorithms

ar.inspiredpencil.com
Schematic Diagram Of Public Key Cryptography – Circuit Diagram

www.circuitdiagram.co
Asymmetric Encryption: Definition, Architecture, Usage

www.okta.com
Public Key Encryption | How Does Public Key Encryption Work?
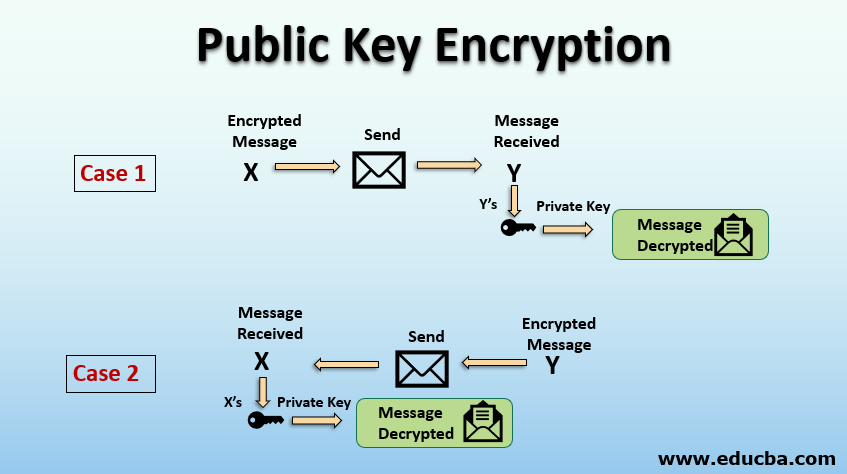
www.educba.com
encryption educba
Schematic Diagram Of Public Key Cryptography – Circuit Diagram

www.circuitdiagram.co
Public Key Cryptography: Private Vs Public | Sectigo® Official

www.sectigo.com
encryption cryptography pki blockchain keys decryption sectigo explained cryptographic encrypt algorithms generate invisible automatically
Public-key Cryptosystem | Download Scientific Diagram

www.researchgate.net
cryptosystem
Public Key Encryption: What Is Public Cryptography? – Okta AU & NZ

www.okta.com
5.: Public-key Cryptography | Download Scientific Diagram

www.researchgate.net
Unit – 4 Cryptography – LearnerBits

learnerbits.com
What Is Public Key Cryptography? – Twilio
www.twilio.com
key cryptography encryption public symmetric tls secret between security private diagram messages who twilio apps chat data end
Public Key Cryptography | Download Scientific Diagram

www.researchgate.net
What Are Basic Cryptography Tools? – Coding Ninjas
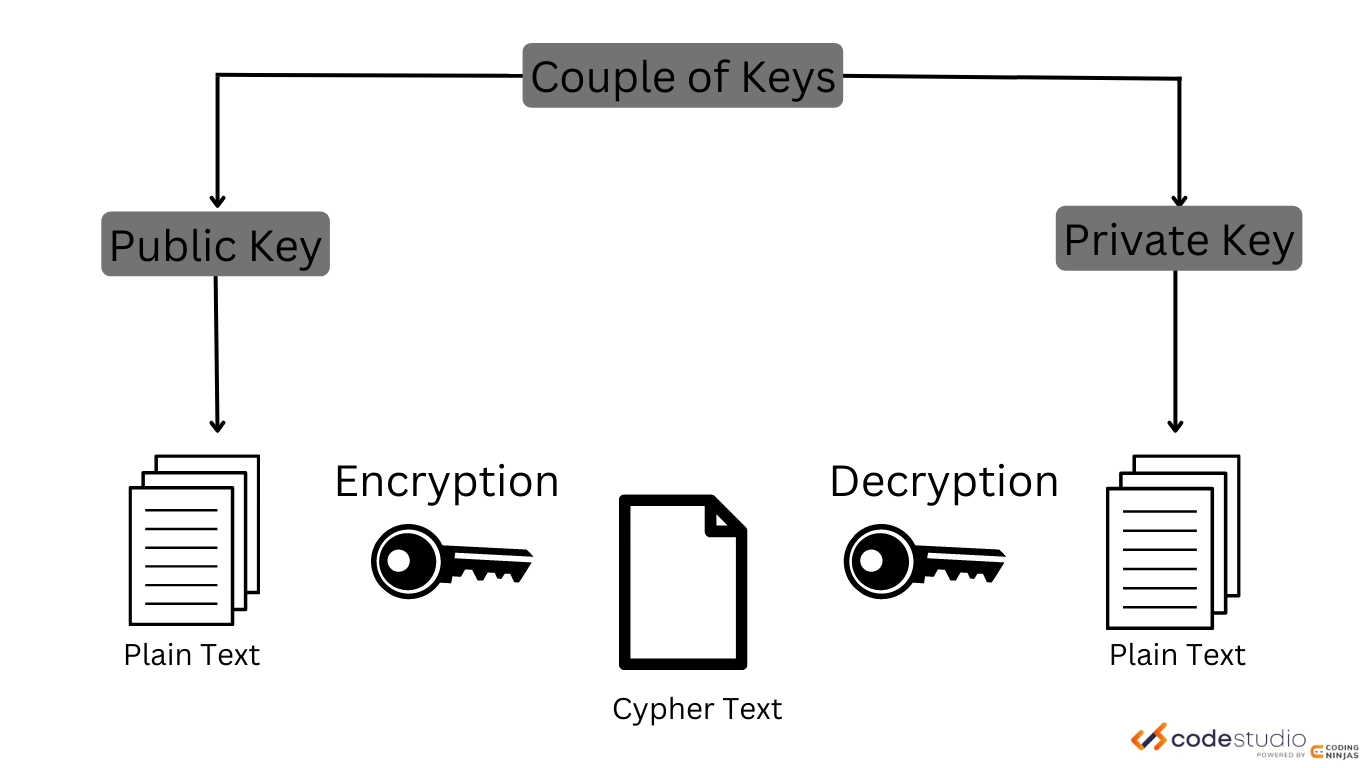
www.codingninjas.com
Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

o3schools.com
symmetric cryptography understanding o3schools
How Does Public Key Encryption Work?

www.securew2.com
encryption does alice decrypt encrypts
Public Key Encryption
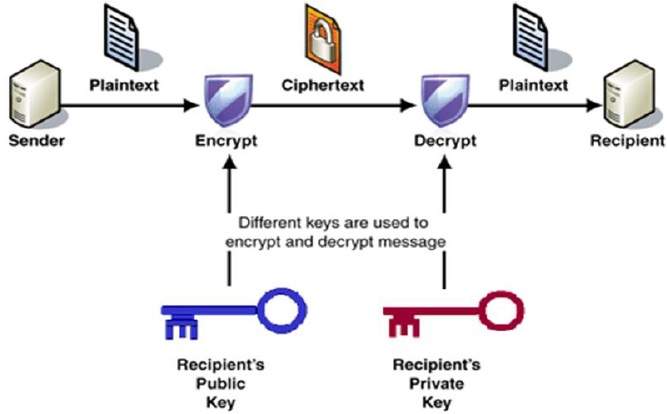
scanftree.com
key public cryptography rsa encryption private cryptosystem algorithm process decryption scheme properties shows explained illustration chapter security network when technological
Public Key Encryption – GeeksforGeeks
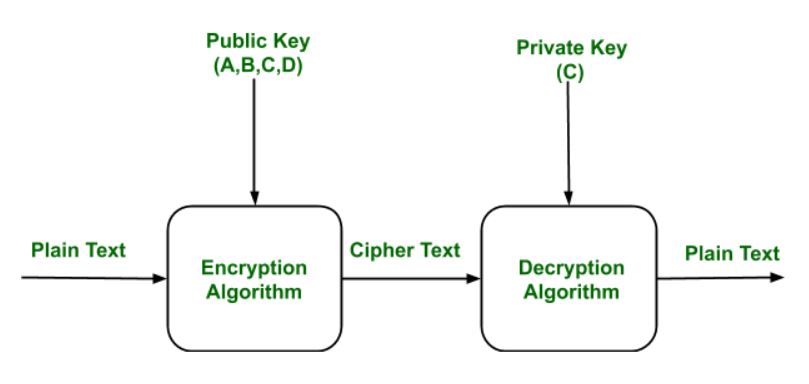
www.geeksforgeeks.org
key public encryption private algorithm geeksforgeeks message generation only
Mechanism Of Public Key Cryptography | Download Scientific Diagram

www.researchgate.net
Public Key Cryptography | Download Scientific Diagram

www.researchgate.net
Public Key Cryptography Algorithms

ar.inspiredpencil.com
Cryptographic Keys 101: What They Are & How They Secure Data – Hashed

www.thesslstore.com
Public Key Cryptography | Download Scientific Diagram
www.researchgate.net
The Math In Public-key Cryptography Explained In Simple Words | By
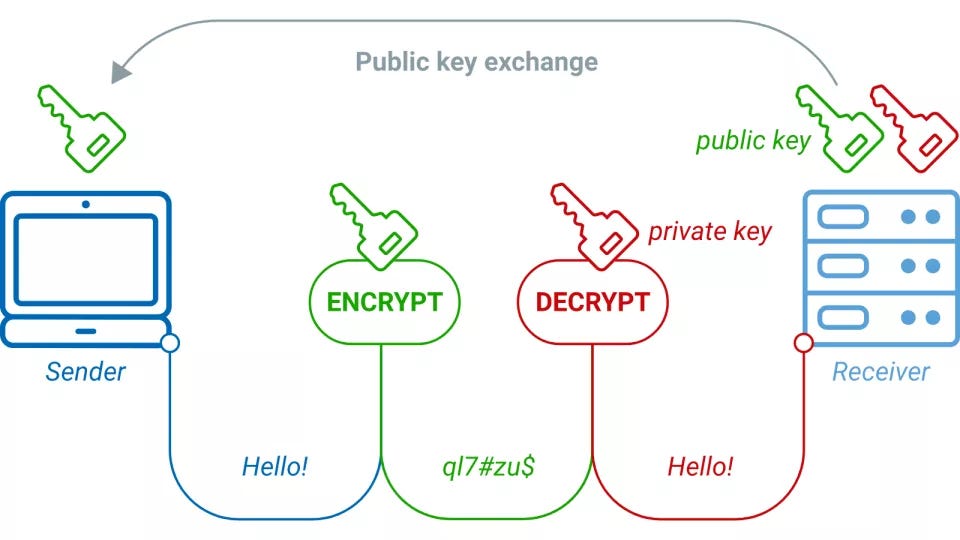
medium.com
Mechanism Of Public-key Cryptography. | Download Scientific Diagram

www.researchgate.net
Public Key Cryptography – NETWORK ENCYCLOPEDIA
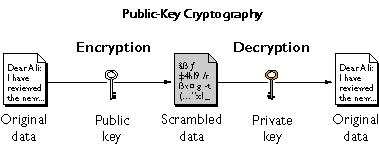
networkencyclopedia.com
cryptography clave dev pico
Public Key Encryption

www.tutorialspoint.com
key public cryptography encryption scheme decryption most illustration
What Is Public Key And Private Key Cryptography, And How Does It Work?

cheapsslsecurity.com
key encryption private public digital does cryptography certificate work keys symmetric email encrypt do signature use security ssl example create
Schematic Diagram Of Public Key Cryptography – Circuit Diagram

www.circuitdiagram.co
Optical Encryption Schematic Based On Ghost Imaging. | Download

www.researchgate.net
Optical encryption schematic based on ghost imaging.. Asymmetric encryption: definition, architecture, usage. Encryption educba
